Explain the social learning theory in details?
![Explain the social learning theory in details?]()
Reviewed by
enakta13
on
December 31, 2012
Rating:
5
Write a note on the managerial roles and skills?
![Write a note on the managerial roles and skills?]()
Reviewed by
enakta13
on
December 31, 2012
Rating:
5
Explain 2-tier and N-tier architecture?
![Explain 2-tier and N-tier architecture?]()
Reviewed by
enakta13
on
December 14, 2012
Rating:
5
Write a program in 8086 assembly language that multiplies two single digit ASCII numbers. You must first convert these ASCII numbers to equivalent binary. The result of the multiplication must be converted to unpacked decimal number. This resultant unpacked binary coded decimal (BCD) number should have its units digit in AL register and tens digit in AX register.

Reviewed by
enakta13
on
November 30, 2012
Rating:
5
What is a crond? What is its use?
![What is a crond? What is its use?]()
Reviewed by
enakta13
on
November 22, 2012
Rating:
5
How will you perform the following in vi?i) To search and replace all occurences of pattern1 with pattern2ii) insert text (and enter input mode)iii) append text (to end of line)iv) Move to beginning of linev) Move to the end of line
![How will you perform the following in vi?i) To search and replace all occurences of pattern1 with pattern2ii) insert text (and enter input mode)iii) append text (to end of line)iv) Move to beginning of linev) Move to the end of line]()
Reviewed by
enakta13
on
November 22, 2012
Rating:
5
Mention few services provided by UUCP with one example.
![Mention few services provided by UUCP with one example.]()
Reviewed by
enakta13
on
November 15, 2012
Rating:
5
Write a simple command and show how a process can be suspended.
![Write a simple command and show how a process can be suspended.]()
Reviewed by
enakta13
on
November 12, 2012
Rating:
5
Explain the significance of option –I, -v with grep command
![Explain the significance of option –I, -v with grep command]()
Reviewed by
enakta13
on
November 12, 2012
Rating:
5
With proper syntax explain the use of chmod command.

Reviewed by
enakta13
on
November 11, 2012
Rating:
5
What do you mean by a Process? What are the various possible states of Process? Discuss

Reviewed by
enakta13
on
November 10, 2012
Rating:
5
What are various File Systems supported in UNIX? Discuss any three of them.
![What are various File Systems supported in UNIX? Discuss any three of them.]()
Reviewed by
enakta13
on
November 10, 2012
Rating:
5
What are the various standards in UNIX? Discuss various features of UNIX.

Reviewed by
enakta13
on
November 10, 2012
Rating:
5
Explain UNIX system architecture.

Reviewed by
enakta13
on
November 10, 2012
Rating:
5
Explain the steps involved in DHCP client/server interaction
![Explain the steps involved in DHCP client/server interaction]()
Reviewed by
enakta13
on
November 08, 2012
Rating:
5
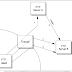
Discuss FTP proxy transfer through firewall
Reviewed by
enakta13
on
October 19, 2012
Rating:
5
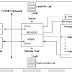
Explain the principle of operation of REXEC protocol.
Reviewed by
enakta13
on
October 19, 2012
Rating:
5
List and explain various fields of HTTP messages
![List and explain various fields of HTTP messages]()
Reviewed by
enakta13
on
October 13, 2012
Rating:
5
Explain the various steps in TCP congestion control.

Reviewed by
enakta13
on
October 08, 2012
Rating:
5
What is fragmentation ? Explain its significations.
![What is fragmentation ? Explain its significations.]()
Reviewed by
enakta13
on
October 06, 2012
Rating:
5
Discuss the characteristics of AAL5.
![Discuss the characteristics of AAL5.]()
Reviewed by
enakta13
on
October 06, 2012
Rating:
5
What do you mean by RFC? Explain its significance
![What do you mean by RFC? Explain its significance]()
Reviewed by
enakta13
on
October 06, 2012
Rating:
5
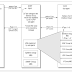
Explain about the SNMP manager.
Reviewed by
enakta13
on
October 03, 2012
Rating:
5
Draw and explain the structure of a web browser.

Reviewed by
enakta13
on
October 03, 2012
Rating:
5
Explain the differences between POP and IMAP4.
![Explain the differences between POP and IMAP4.]()
Reviewed by
enakta13
on
October 03, 2012
Rating:
5
Explain the working of SMTP.
![Explain the working of SMTP.]()
Reviewed by
enakta13
on
October 03, 2012
Rating:
5
Explain the working for passive data connection in FTP.

Reviewed by
enakta13
on
October 03, 2012
Rating:
5
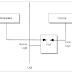
Explain the working of Telnet.
Reviewed by
enakta13
on
October 03, 2012
Rating:
5
Discuss the various steps in domain name resolution.
![Discuss the various steps in domain name resolution.]()
Reviewed by
enakta13
on
October 02, 2012
Rating:
5
Explain Ports and Sockets.
![Explain Ports and Sockets.]()
Reviewed by
enakta13
on
October 02, 2012
Rating:
5
Differentiate UDP and TDP.
![Differentiate UDP and TDP.]()
Reviewed by
enakta13
on
October 02, 2012
Rating:
5
Draw IP datagram format and explain about its each field briefly.

Reviewed by
enakta13
on
October 02, 2012
Rating:
5
What is Point to Point protocol (PPP)? Summarize PPP encapsulation.

Reviewed by
enakta13
on
October 02, 2012
Rating:
5
Draw and explain the architecture of the TCP/IP protocol suite.

Reviewed by
enakta13
on
September 30, 2012
Rating:
5
What is the need of Direct Memory Access (DMA) in a Single User Computer? What is DMA module? Explain the functions of a DMA module.
![What is the need of Direct Memory Access (DMA) in a Single User Computer? What is DMA module? Explain the functions of a DMA module.]()
Reviewed by
enakta13
on
September 21, 2012
Rating:
5
Explain the concept of Direct mapping Cache memory with the help of an diagram/example. How is this Direct mapping cache different to that of 2 way set associative cache memory?

Reviewed by
enakta13
on
September 15, 2012
Rating:
5
Differentiate between the access mechanism of a magnetic disk to that of CD ROM? Why do you need a number of disks (RAID)? Define different levels of RAID?
![Differentiate between the access mechanism of a magnetic disk to that of CD ROM? Why do you need a number of disks (RAID)? Define different levels of RAID?]()
Reviewed by
enakta13
on
September 14, 2012
Rating:
5
Draw the circuit for a decoder and explain the working of this decoder. List the possible uses of the decoder circuit.
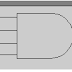
Reviewed by
enakta13
on
September 12, 2012
Rating:
5
What are the micro-instructions? Explain the different types of micros-instructions that can be used in a computer system. Explain the process of micro-instruction execution.
![What are the micro-instructions? Explain the different types of micros-instructions that can be used in a computer system. Explain the process of micro-instruction execution.]()
Reviewed by
enakta13
on
September 11, 2012
Rating:
5
Write a program in 8086 assembly language that multiplies two single digit ASCII numbers. You must first convert these ASCII numbers to equivalent binary. The result of the multiplication must be converted to unpacked decimal number. This resultant unpacked binary coded decimal (BCD) number should have its units digit in AL register and tens digit in AX register

Reviewed by
enakta13
on
September 11, 2012
Rating:
5
What is ERP? Explain its existence before and its future after? What are the advantages & Disadvantages of ERP? What is Artificial Intelligence? How is it different from Neural Networks?
![What is ERP? Explain its existence before and its future after? What are the advantages & Disadvantages of ERP? What is Artificial Intelligence? How is it different from Neural Networks?]()
Reviewed by
enakta13
on
September 09, 2012
Rating:
5
Describe in brief the various phases of the quality control process.
![Describe in brief the various phases of the quality control process.]()
Reviewed by
enakta13
on
September 07, 2012
Rating:
5
Explain the Net operating approach to capital structure
![Explain the Net operating approach to capital structure]()
Reviewed by
enakta13
on
September 05, 2012
Rating:
5
Explain Knowledge based system? Explain DSS and OLAP with example?
![Explain Knowledge based system? Explain DSS and OLAP with example?]()
Reviewed by
enakta13
on
September 04, 2012
Rating:
5
Explain in brief the origins of Just In Time. Explain the different types of wastes that can be eliminated using JIT.
![Explain in brief the origins of Just In Time. Explain the different types of wastes that can be eliminated using JIT.]()
Reviewed by
enakta13
on
August 31, 2012
Rating:
5
Describe the following with suitable examples: A) Modeling the realization of a Use case B) Modeling the realization of an operation C) Modeling a Mechanism
![Describe the following with suitable examples: A) Modeling the realization of a Use case B) Modeling the realization of an operation C) Modeling a Mechanism]()
Reviewed by
enakta13
on
August 30, 2012
Rating:
5
Describe the following: A) Modeling the architecture of a system B) Modeling Systems C) Models and Views D) Traces
![Describe the following: A) Modeling the architecture of a system B) Modeling Systems C) Models and Views D) Traces]()
Reviewed by
enakta13
on
August 29, 2012
Rating:
5
Describe the following with suitable examples: A) Modeling the realization of a Use case B) Modeling the realization of an operation C) Modeling a Mechanism
![Describe the following with suitable examples: A) Modeling the realization of a Use case B) Modeling the realization of an operation C) Modeling a Mechanism]()
Reviewed by
enakta13
on
August 29, 2012
Rating:
5
SYSTEM DESIGN USING MICROCONTROLLER
![SYSTEM DESIGN USING MICROCONTROLLER]()
Reviewed by
enakta13
on
August 29, 2012
Rating:
5
Discuss in detail the Process management, Memory management, I/O and File management and Security and Protection in LINUX Operating System
![Discuss in detail the Process management, Memory management, I/O and File management and Security and Protection in LINUX Operating System]()
Reviewed by
enakta13
on
August 28, 2012
Rating:
5
Describe why authentication is important for file protection.
![Describe why authentication is important for file protection.]()
Reviewed by
enakta13
on
August 28, 2012
Rating:
5
List the security attacks that cannot be prevented by encryption.
![List the security attacks that cannot be prevented by encryption.]()
Reviewed by
enakta13
on
August 28, 2012
Rating:
5
There is a total of 15 units of Rl (resource 1) and 7 units of R2 and the system is in the following state (again call it SO):
![There is a total of 15 units of Rl (resource 1) and 7 units of R2 and the system is in the following state (again call it SO):]()
Reviewed by
enakta13
on
August 28, 2012
Rating:
5
What will be the number of page faults for the algorithms (FIFO, LRU and Optimal) for the following page reference string: 1,2,3,3,5,1,2,2,6,2,1,5,7,6,3 for a memory with 4 frames?
![What will be the number of page faults for the algorithms (FIFO, LRU and Optimal) for the following page reference string: 1,2,3,3,5,1,2,2,6,2,1,5,7,6,3 for a memory with 4 frames?]()
Reviewed by
enakta13
on
August 28, 2012
Rating:
5
Consider the following jobs: Job # Arrival time Run time A05 B24 C35 D53
![Consider the following jobs: Job # Arrival time Run time A05 B24 C35 D53]()
Reviewed by
enakta13
on
August 28, 2012
Rating:
5
State the Readers and Writers Problem and write its semaphore based solution. Also describe the algorithm. Can the producer consumer problem be considered as a special xase of Reader/Writer problem with a single Writer(the producer and a single Reader (consumer) Explain.)
![State the Readers and Writers Problem and write its semaphore based solution. Also describe the algorithm. Can the producer consumer problem be considered as a special xase of Reader/Writer problem with a single Writer(the producer and a single Reader (consumer) Explain.)]()
Reviewed by
enakta13
on
August 28, 2012
Rating:
5
Write about Common Modeling techniques in Relationships
![Write about Common Modeling techniques in Relationships]()
Reviewed by
enakta13
on
August 27, 2012
Rating:
5
Describe the following with respect to Common Modeling Techniques: A) Modeling object Structures B) Forward and Reverse Engineering C) Object Diagrams
![Describe the following with respect to Common Modeling Techniques: A) Modeling object Structures B) Forward and Reverse Engineering C) Object Diagrams]()
Reviewed by
enakta13
on
August 26, 2012
Rating:
5
Discuss the common modeling techniques in UML
![Discuss the common modeling techniques in UML]()
Reviewed by
enakta13
on
August 26, 2012
Rating:
5
Describe the theory and real time applications of Unified Modeling Language (UML)
![Describe the theory and real time applications of Unified Modeling Language (UML)]()
Reviewed by
enakta13
on
August 25, 2012
Rating:
5
division of two 8 – bit numbers using 8051
![division of two 8 – bit numbers using 8051]()
Reviewed by
enakta13
on
August 24, 2012
Rating:
5
multiplication of two 8 – bit numbers using 8051
![multiplication of two 8 – bit numbers using 8051]()
Reviewed by
enakta13
on
August 24, 2012
Rating:
5
Subtraction of two 8 – bit numbers using 8051
![Subtraction of two 8 – bit numbers using 8051]()
Reviewed by
enakta13
on
August 24, 2012
Rating:
5
Addition of 8 – bit numbers using 8051 instruction set
![Addition of 8 – bit numbers using 8051 instruction set]()
Reviewed by
enakta13
on
August 24, 2012
Rating:
5
INTERFACING 8279 KEYBOARD/DISPLAY CONTROLLER WITH 8085 MICROPROCESSOR
![INTERFACING 8279 KEYBOARD/DISPLAY CONTROLLER WITH 8085 MICROPROCESSOR]()
Reviewed by
enakta13
on
August 20, 2012
Rating:
5
INTERFACING ADC WITH 8085 PROCESSOR
![INTERFACING ADC WITH 8085 PROCESSOR]()
Reviewed by
enakta13
on
August 20, 2012
Rating:
5
SQUARE OF A NUMBER USING LOOK UP TABLE
![SQUARE OF A NUMBER USING LOOK UP TABLE]()
Reviewed by
enakta13
on
August 20, 2012
Rating:
5
ASCII TO HEX CONVERSION
![ASCII TO HEX CONVERSION]()
Reviewed by
enakta13
on
August 20, 2012
Rating:
5
HEX TO ASCII CONVERSION
![HEX TO ASCII CONVERSION]()
Reviewed by
enakta13
on
August 20, 2012
Rating:
5
HEX TO BCD CONVERSION
![HEX TO BCD CONVERSION]()
Reviewed by
enakta13
on
August 20, 2012
Rating:
5
BCD TO HEX CONVERSION
![BCD TO HEX CONVERSION]()
Reviewed by
enakta13
on
August 20, 2012
Rating:
5
ARRANGE AN ARRAY OF DATA IN DESCENDING ORDER
![ARRANGE AN ARRAY OF DATA IN DESCENDING ORDER]()
Reviewed by
enakta13
on
August 17, 2012
Rating:
5
ARRANGE AN ARRAY OF DATA IN ASCENDING ORDER
![ARRANGE AN ARRAY OF DATA IN ASCENDING ORDER]()
Reviewed by
enakta13
on
August 17, 2012
Rating:
5
SMALLEST NUMBER IN AN ARRAY OF DATA
![SMALLEST NUMBER IN AN ARRAY OF DATA]()
Reviewed by
enakta13
on
August 17, 2012
Rating:
5
LARGEST NUMBER IN AN ARRAY OF DATA
![LARGEST NUMBER IN AN ARRAY OF DATA]()
Reviewed by
enakta13
on
August 17, 2012
Rating:
5
DIVISION OF TWO 8 BIT NUMBERS
![DIVISION OF TWO 8 BIT NUMBERS]()
Reviewed by
enakta13
on
August 17, 2012
Rating:
5
MULTIPLICATION OF TWO 8 BIT NUMBERS
![MULTIPLICATION OF TWO 8 BIT NUMBERS]()
Reviewed by
enakta13
on
August 17, 2012
Rating:
5
SUBTRACTION OF TWO 8 BIT NUMBERS
![SUBTRACTION OF TWO 8 BIT NUMBERS]()
Reviewed by
enakta13
on
August 17, 2012
Rating:
5
ADDITION OF TWO 8 BIT NUMBERS
![ADDITION OF TWO 8 BIT NUMBERS]()
Reviewed by
enakta13
on
August 17, 2012
Rating:
5
![Explain the social learning theory in details?]() Reviewed by enakta13
on
December 31, 2012
Rating:
Reviewed by enakta13
on
December 31, 2012
Rating:

















